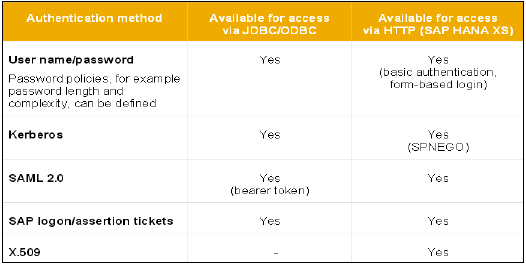
All SAP HANA users that have access on HANA database are verified with different Authentications method. SAP HANA system supports various types of authentication method and all these login methods are configured at time of profile creation.
Below is the list of authentication methods supported by SAP HANA −
- User name/Password
- Kerberos
- SAML 2.0
- SAP Logon tickets
- X.509
User Name/Password
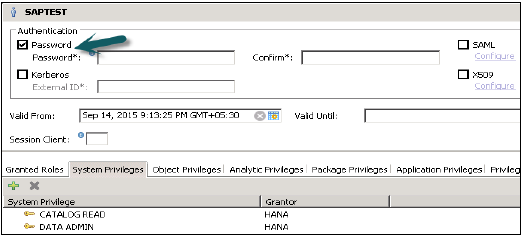
This method requires a HANA user to enter user name and password to login to database. This user profile is created under User management in HANA Studio → Security Tab.
Password should be as per password policy i.e. Password length, complexity, lower and upper case letters, etc.
You can change the password policy as per your organization’s security standards. Please note that password policy cannot be deactivated.
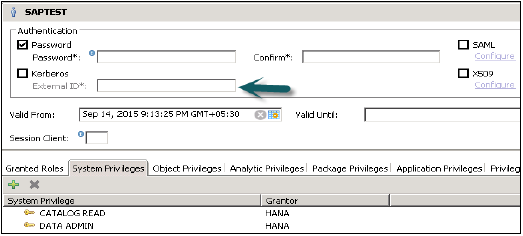
Kerberos
All users who connect to HANA database system using an external authentication method should also have a database user. It is required to map external login to internal database user.
This method enables users to authenticate HANA system directly using JDBC/ODBC drivers through network or by using front end applications in SAP Business Objects.
It also allows HTTP access in HANA Extended Service using HANA XS engine. It uses SPENGO mechanism for Kerberos authentication.
SAML
SAML stands for Security Assertion Markup Language and can be used to authenticate users accessing HANA system directly from ODBC/JDBC clients. It can also be used to authenticate users in HANA system coming via HTTP through HANA XS engine.
SAML is used only for authentication purpose and not for authorization.
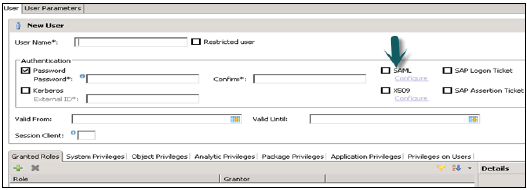
SAP Logon and Assertion Tickets
SAP Logon/assertion tickets can be used to authenticate users in HANA system. These tickets are issued to users when they login into SAP system, which is configured to issue such tickets like SAP Portal, etc. User specified in SAP logon tickets should be created in HANA system, as it does not provide support for mapping users.
X.509 Client Certificates
X.509 certificates can also be used to login to HANA system via HTTP access request from HANA XS engine. Users are authenticated by certificated that are signed from trusted Certificate Authority, which is stored in HANA XS system.
User in trusted certificate should exist in HANA system as there is no support for user mapping.
Single Sign On in HANA system
Single sign on can be configured in HANA system, which allows users to login to HANA system from an initial authentication on the client. User logins at client applications using different authentication methods and SSO allows user to access HANA system directly.
SSO can be configured on below configuration methods −
- SAML
- Kerberos
- X.509 client certificates for HTTP access from HANA XS engine
- SAP Logon/Assertion tickets




0 Comments:
Post a Comment