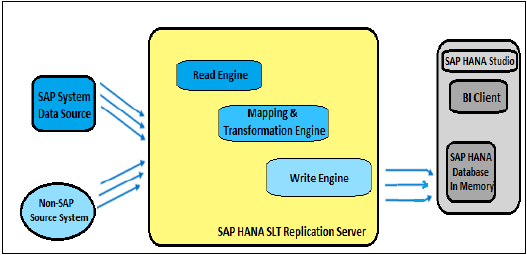
SAP HANA ETL based replication uses SAP Data Services to migrate data from SAP or non-SAP source system to target HANA database. BODS system is an ETL tool used to extract, transform and load data from source system to target system.
It enables to read the business data at Application layer. You need to define data flows in Data Services, scheduling a replication job and defining source and target system in data store in Data Services designer.
How to use SAP HANA Data Services ETL based Replication?
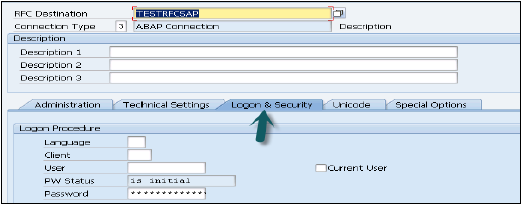
Login to Data Services Designer (choose Repository) → Create Data store
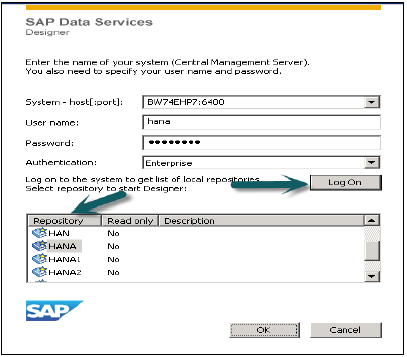
For SAP ECC system, choose database as SAP Applications, enter ECC server name, user name and password for ECC system, Advanced tab choose details as instance number, client number, etc. and apply.

This data store will come under local object library, if you expand this there is no table inside it.
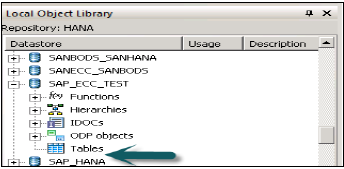
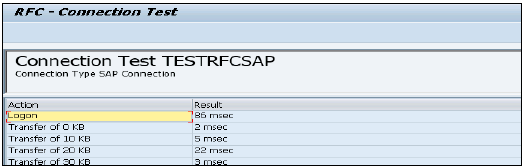
Right click on Table → Import by name → Enter ECC table to import from ECC system (MARA is default table in ECC system) → Import → Now expand Table → MARA → Right Click View Data. If data is displayed, Data store connection is fine.
Now, to choose target system as HANA database, create a new data store. Create Data store → Name of data store SAP_HANA_TEST → Data store type (database) → Database type SAP HANA → Database version HANA 1.x.
Enter HANA server name, user name and password for HANA system and OK.
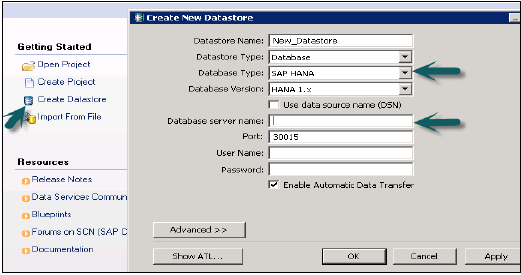
This data store will be added to Local Object Library. You can add table if you want to move data from source table to some specific table in HANA database. Note that target table should be of similar datatype as source table.
Creating a Replication Job
Create a new Project → Enter Project Name → Right Click on Project name → New Batch Job → Enter job name.
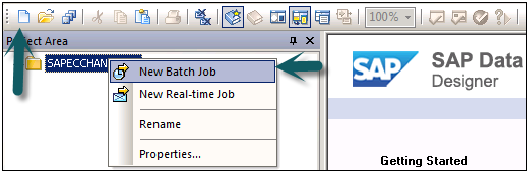
From right side tab, choose work flow → Enter work flow name → Double click to add it under batch job → Enter data flow → Enter data flow name → Double click to add it under batch job in Project area Save all option at top.
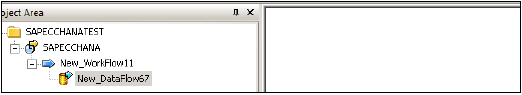
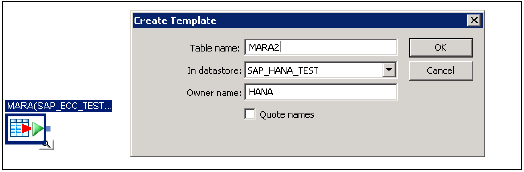
Drag table from First Data Store ECC (MARA) to work area. Select it and right click → Add new → Template table to create new table with similar data types in HANA DB → Enter table name, Data store ECC_HANA_TEST2 → Owner name (schema name) → OK
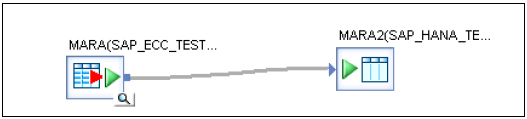
Drag table to front and connect both the table → save all. Now go to batch job → Right Click → Execute → Yes → OK
Once you execute the Replication job, you will get a confirmation that job has been completed successfully.
Go to HANA studio → Expand Schema → Tables → Verify data. This is manual execution of a batch job.
Scheduling of Batch Job
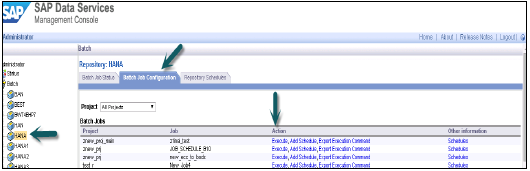
You can also schedule a batch job by going to Data Services Management console. Login to Data Services Management Console.
Choose the repository from left side → Navigate to 'Batch Job Configuration' tab, where you will see the list of jobs → Against the job you want to schedule → click on add schedule → Enter the 'schedule name' and set the parameters like (time, date, reoccurring etc.) as appropriate and click on 'Apply'.